Home → News & Resources → Experts Talk
Building your data protection foundation by using the ISO/IEC 27701 core components
- Updated | 2022-09-13
Even 6 years after the publication of the GDPR and 4 years after its activation, many companies in various sectors do not succeed to get the data protection basics right, let alone they get their enterprise information security under control.
More specifically, SMBs (small and medium business) struggle to meet the bar for minimum compliance with GDPR and other data protection regulations.
Many of these businesses think they lack the knowledge to do it right. Therefore, many management teams overestimate the amount of work needed for basic compliance or do not know how and where to start.
At first sight, they think implementing an ISO/IEC 27001 (ISMS) and by extension ISO/IEC 27701 (PIMS) is an insurmountable job and they quit before starting.
NOTE: ISMS stands for Information Security Management System and PIMS is Privacy Information Management System, which is an extension of ISMS.
It is important to know that these ISO standards are built on the PDCA (Plan-Do-Check-Act) principle.
That allows you to break down the work in small workable pieces to build up the management system and keep improving it, step by step, in a very practical way.
Before we explore the pieces of the puzzle you need, there are a few basic principles you need to remember.
The purpose of this article
In this article, we will use the ISO/IEC 27701 with a limited scope, and look at the minimal requirements to implement the critical parts for handling the subject rights.
We will be picking the minimum actions and requirement to implement a basic data protection program in order to produce a privacy notice on your website and to organize the basic processes and procedures that allow you to handle data protection incidents (data breaches), to respond to inquiries by stakeholders and get in control of your data protection. To start with a data processing register, an incident management system, managing access requests and a privacy notice.
And of course, it will provide you with a baseline security you can build on for the next steps.
Before you start, know the main principles
Say what you do and do what you say.
It is important to maintain documentation and evidence of what you do. This is an important foundation to maintain and share knowledge. Additionally, whenever it goes wrong, you can use that documentation and evidence to prove that you are in control and that you have implemented security and data protection up to the current standard. This will protect your accountability and responsibility, which will be a major help to protect you in the aftermath of an incident (or data leak).
Raise the bar with “security by design”
One of the main goals of implementing ISMS/PIMS, is to build security and data protection into the DNA of your management system and the company operations, at all levels.
This is what is called “data protection by design” (GDPR) or “security by design” (ISMS/PIMS).
Treat both your enterprise data and personally identifiable information (PII) with the best protection possible, from the start.
Think big, start small
You should always keep the big picture, a helicopter view of your management system, driven by your company business. But the implementation should be practical and focused on results. ISMS or PIMS must not be a paper elephant but a guideline to build an effective (results based) security and data protection system. Sometimes, you need to balance between an administrative system (documentation, evidence) and practical, sustainable security.
Keep improving
One of the essential pillars of an ISO system is continuous improvement (Clause 5.8 of PIMS, equivalent to clause 10 in ISMS), implement the security step-by-step, learning from your mistakes and use the lessons-learned as guide to get better in the next cycle.
Data minimization
You do not need to protect data you do not have.
Design your system to have the minimum data needed. This is important at various stages of the system lifecycle, not only at the design stage, but also during changes, continuous monitoring and when the system is deprecated.
The ISO approach - PDCA
We suppose you are familiar with PDCA (Plan-Do-Check-Act). It is a general approach to (1) first think and plan, then (2) implement. While planning you already think about (3) measuring your progress (check) and (4) based on your measurement adapt your system (act) to integrate improvement.
If PDCA does not ring a bell, check the ISO 9001:2015 (figure 1), which is the mother standard for many management systems.
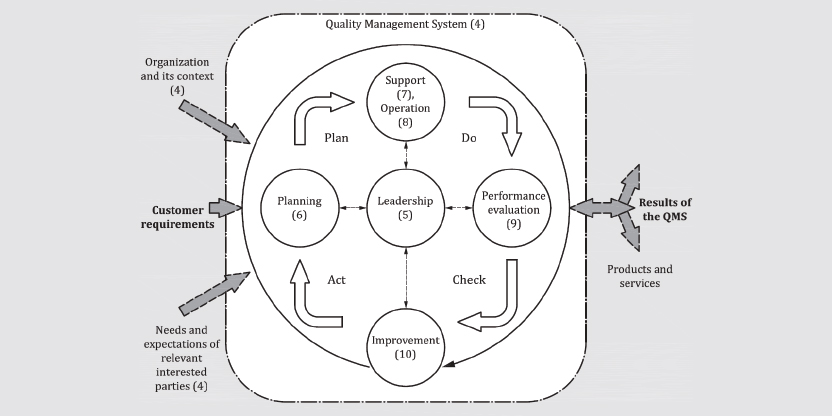
Figure 1: Plan-Do-Check-Act cycle from ISO 9001:2015 Chapter 0.3.2 (Source: ISO Standards)
Here is a very straight forward approach (figure 2) to cover these steps, which contains easy to understand steps.
-
- Plan (define and establish),
- Do (implement and operate),
- Check (monitor and review),
- Act (maintain and improve).
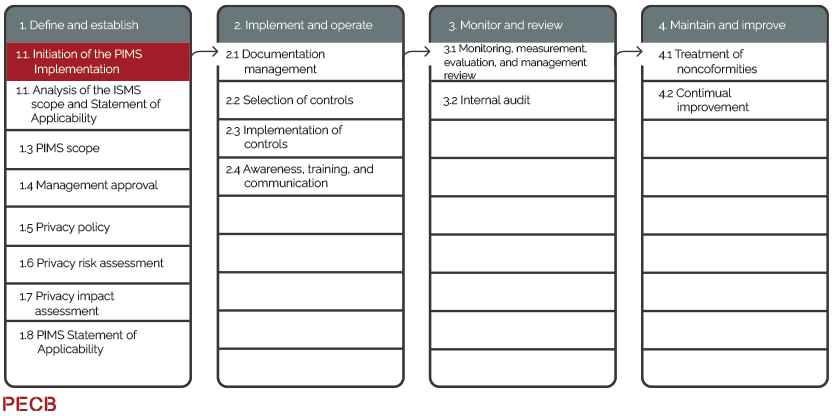
Figure 2: Plan-Do-Check-Act cycle from PECB ISO 27701 Lead Implementer Course
For this article, we will only implement the relevant steps, to have a light weight foundation. In the next cycles of your PIMS/ISMS implementation you will add more detailed steps to increase maturity.
Where to start? Knowing your context.
1. Know and document your (personal data) stakeholders
Reference: ISO/IEC 27701 Clause 5.2 (ISO/IEC 27001 Clause 4)
Before you can implement any system, you need to analyze and investigate the stakeholders that influence your security and data protection in one way or another. This influence can be active or passive, direct or indirect, internal or external to the organization.
This is exactly what is indicated in previous imaged of the PDCA, on the left hand side:
- The organization and its context,
- Customers and their requirements,
- The needs and expectations of relevant interested parties
Listing the interested parties, understanding their data and mapping your interests & obligations will allow you to quickly understand the impact of an incident or data breach.
Task: Make a list of all people categories involved, directly or indirectly, internal or external, professional or personal.
This can be (but not limited to):
- Internal staff (employee, interims),
- External staff (contractors),
- Vendors, partners,
- Prospects & web site visitors,
- Customers,
- Job candidates,
- Contacts,
- Visitors.
2. Know their data (attributes)
A second part of the data mapping is to list the data attributes you use of the subjects that identifies or can identify these people. Typically:
- First name & last name,
- Contact data (mail, phone, direct messaging),
- Personal address data
But also think about more critical data like:
- Governmental ID (ID card, eID),
- Sensitive data (check GDPR Art. 9), include health data.
Task: Start to create a processing register, including the subject types and their attributes. How you start is not important, even a simple Excel tabular sheet will do, as long as you start managing it.
3. Know and document your relation to the data
Reference: This is covered in the ISO/IEC 27701 Clause 7.2.2 (Identify lawful basis).
It is extremely important to know why you need these data sets. What is the reason for processing information? For each process that handles data you should know the purpose definition, referring to the GDPR Art 6: Performance of a contract; Compliance with legal obligations; Protection of vital interest of the PII Principals (subjects); Performance of a task of public interest; Consent of the PII Principal (subject); Legitimate interest of PII controller.
Important note here: please be aware that legitimate interest and subject consent can be withdrawn or cancelled any time, these are pretty weak reasons to process data. An important hint here is to design processes with relation to consent or legitimate interest in a thorough, well documented way…(and only use them if no other option is possible).
4. Know how you collect and receive the data and how you transfer it to other parties
Reference: ISO/IEC 27701 Clause 6.10.2 and additional guidance in Clause 7.2.7 (Joint PII controller)
Tasks:
- Run a DPIA/PIA risk analysis on the data processing.
- Build and maintain a processing register with a data flow.
There are a few reasons why you should carefully map the data flows and keep this mapping up to date. ISO/IEC 27701 Clause 7.5 handles “PII sharing, transfer, and disclosure”, and sets some requirements that you need to cover to manage PII transfers.
- Identify the reason for international transfers (Clause 7.5.1),
- Identify 3rd countries, applicable legislation and jurisdiction (Clause 7.5.2),
- Maintain PII transfer records (Clause 7.5.3),
- Maintain PII disclosure records (Clause 7.5.4).
First of all, when an incident of data breach happens, you should be able to find out which data is impacted by the data breach.
Additionally, if the data flows change or the conditions for processing the data change, you need to get in touch with the data providers and the receiving parties. It is an essential responsibility as PII controller to keep control.
You should also be able to show evidence when and where you disclosed which information to thirds parties.
ISO/IEC 27701 Clause 7.2.7 provides interesting guidance on building a PII controller agreement.
Take special care managing consent and legitimate interest
Reference: ISO/IEC 27701 Clause 7.2.4 (Obtain and record consent)
The clause says: “The organization should obtain and record consent from PII principals according to the documented processes.”
You need to take special care when handling data under consent, as the ISO/IEC 27701 explains:
“The consent should be:
- freely given,
- specific regarding the purpose for processing; and
- unambiguous and explicit”
Furthermore, consent can be withdrawn, so it is a very volatile situation you need to handle correctly.
As “legitimate interest” is a decision made by the PII controller, possibly without interaction to the subject, it is highly advised to document this process in detail, why and how you contact the subject, and also, very important, how you collected their data.
In most cases, legitimate interest can be overridden by the subject right to stop processing the data.
DPO or no DPO is not the question…
Although GDPR itself is very clear when you need to appoint a DPO (data protection officer), you will notice that this requirement is rather limited, in short
- when the organization is a public authority,
- the core activities of the controller or processor consist of regular and systematic monitoring of subjects at
- large scale,
- large scale processing of sensitive data.
From this point of view, there is no strict need to assign a specialist or an advisor but this creates important risks and issues if you choose not to assign a DPO, CPO (chief privacy officer) of what ever you want to name it.
That is where ISO/IEC 27701 makes a difference, referring to clause 6.3.1.1 (Information security roles and responsibilities).
“The organization should designate a point of contact for use by the customer regarding the processing of PII. When the organization is a PII controller, designate a point of contact for PII principals regarding the processing of their PII (see 7.3.2).
The organization should appoint one or more persons responsible for developing, implementing, maintaining and monitoring an organization-wide governance and privacy program, to ensure compliance with all applicable laws and regulations regarding the processing of PII.”
Task: Make sure to have a trained and seasoned data protection specialist available that can advise on implementing and maintaining the privacy and data protection program. This can be internal, external, full time, part-time, it is up to you to decide what support you need. But keep in mind that if you need support after the facts, it is going to cost you x times more than the when take care of it from the start.
Managing data protection operations
Again, the purpose of this article is NOT to fully cover the ISMS nor PIMS implementation in detail. There is an awful lot of work to build a mature system.
But there are at least 2 important operations that will require special attention:
- management of data access requests,
- incident & data breach management.
The simple reason is that in many legislations there are specific requirements on handling subject access request or data breaches.
Remember, for example in GDPR you’ve got 30 days to respond to an access request (extension if there are important reasons) or 72 hours to report a data breach to the data protection authority, but not necessarily to the subjects.
Although these processes are critical and required a planning, many companies fail to implement these procedures. You can guess the consequences…(up to a few 10.000’s of Euros fines..).
Remember that failing to comply with the essential subject rights in GDPR can go up to 4% of your global turn-over or €20M. So it does make sense to pause for implementing an subject access request response procedure, an incident management, a data breach response procedure, right?
Managing access requests
Source:
– In general ISO/IEC 27701 Clause 7.3 Obligations to PII principals.
– More specific: Clause 7.3.8 (Providing copy of PII processed), Clause 7.3.9 (Handling requests)
In many cases, the subject rights are the core driver for the legislation and rules. Therefore many regulations or contracts have penalties and fines covering this requirement. Better take it seriously.
On the other hand, there are a few simple tips & tricks that can help you to manage these requirements.
- As we discussed earlier, it is essential to have a processing register including data flow documentation.
- Make sure to offer the PII principals (subject) an easy and direct communication path to make sure subjects can contact you in the easiest way possible, by preference via e-mail, via a webform.
- Make sure to publish your contact details in the channels you use to communicate with your subjects.
- Keep your contact details up to date.
- When you receive a data access request, immediately send an acknowledgment of receipt. It is an important part of evidence later on. A simple auto reply on mail could do.
- Make sure you understand what the question is. Better ask for clarification if you do not
- Where possible let the subjects manage their profiles and personal data themselves, e.g. provide a customer profile on your web portal. The less you need to do yourself, the more you automate, the better.
- If you experience trouble responding within the required time frames, inform the subject upfront and follow up closely and directly with the subject. We will discuss the importance of clear and transparent communication later on.
Managing incidents & data breaches
Reference: ISO/IEC 27701 Clause 6.13 (linked to ISO/IEC 27001 A16)
While the subject access request or information request is a fairly normal administrative business process, the incident management process is not.
Because an incident is by default an error situation, where the system fails. And depending the impact of the issue, the incident might (quickly) turn into a breach or even a disaster, with high impact to the enterprise.
Therefore, it is essential to be well prepared for incidents and data breaches as an incident should trigger an enterprise to review the PIMS/ISMS and processes.
IMPORTANT: Please consider every incident as an opportunity for improvement, to avoid repetition.
As explained by the ISO/IEC 27701 (Clause 6.13.1.5): “Some jurisdictions define cases when the breach should be notified to the supervisory authority, and when it should be notified to PII principals”.
So it is essential to maintain an up to date contact list, including the data protection authority, data processors, other data controllers.
Furthermore, in case of incidents and data breaches, you should carefully keep records including:
- Incident description,
- Time of occurrence,
- Duration,
- Consequences and impact of the incident,
- Who reported the incident,
- Who received the incident notification/reports,
- Steps taken to follow up and solve the issue.
Please be aware that in some circumstances you might be facing further investigation (forensics) by police cybercrime units, data protection authority or insurance company.
Therefore, you must carefully protect and safeguard evidence.
One of the major risks in case of incidents and disasters, you might risk to lose or damage essential data if you fail to properly manage the situation.
Make sure you are prepared, including performing exercises.
Do not underestimate the power of “muscle memory”, having hands-on experience.
Building smart communication – maintaining customer relations
Incident management, business continuity and disaster recovery require strictly controlled communication management. Not only to make sure the actions are executed as planned to guarantee results, but also to keep all interested parties informed.
Well managed communications allow the stakeholders to keep faith and trust in the enterprise handling the incidents.
But it is difficult to maintain a balanced flow of information to the stakeholders. If you provide too much or not enough information, stakeholders might lose trust in your company. This might cause additional damage to your company, while you are already in a difficult situation.
Imagine what happens within people are disgruntled: they might use social media to vent their frustration or they file a complaint with the data protection authority causing even more administrative overhead for you.
Some practical hints and tips (some more can be found in the ISO/IEC 27035):
- Assign a dedicated crisis communication team.
- Setup and exercise communication and incident response plans.
- Only provide the minimum information needed to the communications team.
- Do not put an IT technician in charge of communications.
- Measure the efficiency and effectiveness of the communications (Do you get the expected feedback?)
Online privacy notice
While the security and data protection baseline you have built so far is purely maintained within the company, and usually not fit for direct publication, it needs an online extension.
For most of your customers, prospects and external stakeholders the first point of contact is your website. You will need to extract a public copy of your processing register to build an online privacy or data protection notice. This is not part of the ISO/IEC 27701 (PIMS), but handled by ISO/IEC 29184 which is part of the ISO/IEC 29100 privacy framework.
Remember: PIMS is the transforming ISMS in to a management system for the privacy framework and GDPR
The good news is, all the ground work you have done so far will be the source for your online privacy notice, and ISO/IEC 29184 provides a check list to build the online privacy notice, including:
- Identification of the PII controller,
- Applicable PII principals (the subjects in the GDPR),
- Purpose description,
- Basis for processing,
- PII collected,
- Collection methods and timing,
- Processing methods,
- PII processors and Third parties involved,
- PII participation (a.k.a. GDPR subject rights),
- Incident management (GDPR data breach procedure),
- Applicable legislation & jurisdiction,
- Inquiry and complaints, incl. Contact with DPA (Data protection authority).
Build maturity, keep going, start over again
As mentioned earlier, this article is a quick start and focused on some essential data protections services, it is not meant to discuss the ISO/IEC 27701 in detail. There is more work to do. For most companies it takes a few years to get a mature, full blown PIMS or ISMS system in place. The PDCA approach integrated in the ISO standard is perfectly fit to build your management system, step by step, in a controlled way. At least get started with ISMS/PIMS, that is the biggest and most important step. Because not implementing an information security and personal information management system will cost you, eventually.
Thinking about certification?
The current status of cybercrime and the continuous cyberattacks and data leakages are putting an increasing stress on business to keep their data safe. More and more customers are demanding for proof that their vendors treat their data with the up-to-date security practices. And of course legislation is following, slowly. It will become more and more important to prove, based on evidence that you are in control. Then certification comes into the picture, not only to prove compliance but to prove that you have build information security and data protection in the DNA of your company.
The ISO/IEC 27701 is a certifiable standard, you can have it audited and get rewarded for it by a Management System Certification Body.
You should know that the ISO/IEC 27701 (PIMS) is not a stand-alone standard, you cannot simply implement “just the ISO/IEC 27701 standard”.
PIMS is an add-on of the ISO/IEC 27001 (ISMS) and requires the ISMS standard implemented.
ISMS already certified
So, if you already have an ISMS certified, you can add the data protection layer on top of it.
Note: The ISO/IEC 27006 audit standard defines the number of audit days required. The number of audit days also depends on the audit cycle (yearly surveillance 1/3 of initial audit, recertification typically 2/3 of initial audit).
A bit of smart planning can save money: if you inject the add-on certification on the right moment, you can easily combine the ISO/IEC 27001 audit with the PIMS add-on.
Certifying PIMS
If you do not have ISO/IEC 27001 (ISMS) certification yet, there are only 2 choices:
- Combine the ISMS/PIMS certification in the same cycle, which is a bit more work, or,
- You certify your ISMS first and then add PIMS on top of it at a later stage (back to the discussion in previous paragraph).
References and standards you need
To implement the data protection essentials, we have been using the following implementation guidance documents and references:
- ISO/IEC 27701
- ISO/IEC 27001
- ISO/IEC 29100 and ISO/IEC 28151
- ISO/IEC 29184
- ISO/IEC 27035 (Incident management)
- GDPR
And also ISO/IEC 27006 for audit guidelines.
In a nutshell
- Get started! Doing nothing will cost you.
- Know your audience: Think about the data of customers, prospects, website visitors, employees, external and temporary staff.
- Know your data and their data: HR data, sensitive data, address, contact details, CV, credentials, anything that identifies or can identify person.
- Manage your communications: Your audience will appreciate your clear, transparent and active communications. It is a strong parameter of trust, even in case of issues.
- Plan for incidents and data breaches: Do not panic – Things WILL go wrong, be prepared. Panic is the worst advisor. A thorough preparation and exercises will save money, time and reputation.
- Every incident is an opportunity for improvement: Learn from your mistakes.
- Start over again (continuous improvement): There is more work to do.
Want to know more?
- About ISO/IEC 27701: What is ISO/IEC 27701
- About MSECB Audit and Certification Process: Getting Familiar with the Certification Process
About Author

Peter Geelen is the owner & managing consultant at Quest for Security & Partner at Cyberminute, Belgium. With over 20 years of experience, Peter built a strong experience in enterprise security & architecture, identity & access management, including privacy, information & data protection, cybersecurity & cloud security. He’s accredited trainer in these areas. Peter is a certified and accredited auditor for ISO/IEC 27001, ISO/IEC 27701, ISO/IEC 22301 & ISO/IEC9001. Peter is constantly exploring new grounds on legislation & certification of products, services & processes in cyber and data protection.
About MSECB
MSECB is specialized in the certification of management systems on a wide range of international standards. As a global provider of audit and certification services, MSECB offers its expertise on multiple fields, including but not limited to Information Security, Quality Management, Business Continuity, Service Management, Health, Safety and Environmental Management. MSECB provides certification services in accordance with ISO/IEC 17021 and ISO/IEC 17065.


